Wipedrive 5 Serial
What Are the Different Forms of Data Destruction? When you see the words 'data destruction', does your heart skip a beat? Do you automatically think of losing important files, having to re-write reports and emails, etc.? Well, if your hard drive gets wiped by mistake, that's one case of data destruction, but in this article, we'll be talking about destroying your data on purpose for your security. Believe it or not, you don't always want it to be easy to retrieve deleted information. While you might have been glad, at one point or another, that you could get back information that you accidentally deleted, that's not always going to be the case. If you're retiring, selling, donating, or otherwise trashing your old hardware, you won't want anyone else to be able to access the data you have saved there.

Data destruction services are invaluable when a person or business decides to upgrade or replace their hardware. It's also often necessary for businesses when they move employees around and/or give them new laptops, desktops, tablets, and/or phones. It's important for both individual security and to protect against identity theft or corporate espionage. Now that we've discussed why you might want to make your data disappear, let's go over the three most commonly used forms of data destruction, how they work, and their advantages and disadvantages. Anjan cut songs free download mp3. Overwriting Data Overwriting data is the process of writing new data on top of old data with the goal of completely removing the old data by using the same space it was stored on for the new data.
Overwriting data is analogous to recording over an old VHS tape. By recording over old content, you destroy it in the process. Because this process erases the old material and renders anything left completely unreadable, this form of data destruction is also called data wiping. When data is overwritten, a pattern of 1s and 0s is written over the original information. Sometimes a random pattern is used but a set pattern can also be used which allows for later verification that the drive was wiped by detecting the set pattern. Overwriting data once is enough for most situations. However, for high security applications multiple wipes may be required.
Wipedrive 5 Serial Code
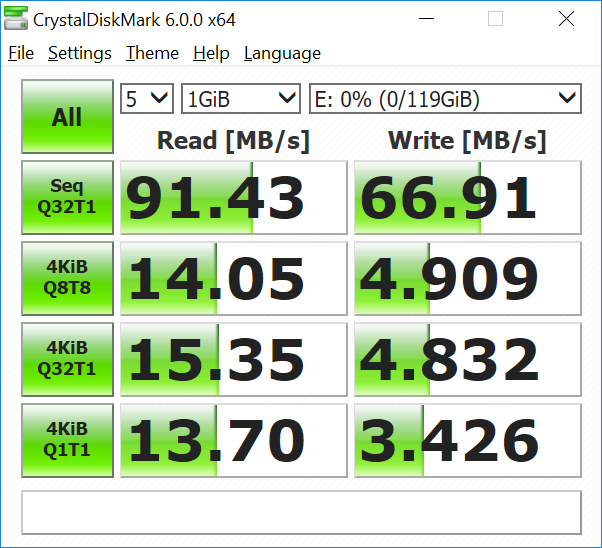
Insert the WipeDrive CD (or floppy diskette) and restart the computer. See 4.1 Wiping a Hard Drive. 3.5 Enabling and Disabling Drives. Some computers have a USB keyboard instead of the standard ps/2 (serial) keyboard. If using a USB Keyboard and WipeDrive does. WipeDrive Home is the ultimate data erasure and drive sanitization tool for individuals and families.Missing.
This provides an extra measure of surety that the old data is destroyed and that there are no bit shadows present. A bit shadow is a remnant of a bit that has been overwritten and can sometimes be detected using a high-power or electron microscope. Bit shadows are a little like the remnants of a chalk board. Even after writing on a chalk board has been erased and written on top of, Sometimes it is still possible to see through the writing enough to make out what was there previously. Only the highest security applications need worry about bit shadowing since recovering data with this method would be very time consuming and expensive using specialized technicians and equipment. Degaussing Degaussing is a method of data destruction that uses a high-powered magnet to disrupt the magnetic field of the storage medium and destroy the data in the process.
While degaussing can be an effective method of data destruction there are two major disadvantages. First, degaussing renders the hard drive inoperable by physically disrupting the delicate interconnected mechanisms of the drive. Since hard drives rely upon precise physical movement and alignment, any small change to this system is enough to ruin a drive. Second, there is no way to ensure all data is destroyed. Because degaussing renders a drive inoperable, there's no way to run the drive to verify the data is gone. You could use forensic methods to verify the data is erased, such as an electron scanning microscope, but these methods are too expensive to be practical in most cases. Physical Destruction If you don't need to reuse hard drives, physical destruction is a possible data destruction option.
There are many methods of physical destruction. Degaussing can be considered physical destruction. Shredding or pulverizing a hard drive uses specialized high-powered equipment to turn a drive into scrap and is one of the most common forms of physical destruction. Other methods include drilling holes in a drive, hammering a drive, or even shooting a drive. Any method that renders the drive inoperable could be considered physical destruction.
There can be major problems with physical destruction. First, it is prone to human error and manipulation. There is no reliable way to audit the physical destruction process. Typically a technician will scan or record a hard drive serial number before destroying a drive. But what's to prevent the technician from forgetting to scan a drive or, even worse, scanning the drive and then not destroying it? Second, most methods of physical destruction leave large portions of the drive platter intact, even if the drive is inoperable.
Wipedrive 5 Serial Numbers
As previously discussed, data could still be recovered using forensic methods in such cases. Only pulverizing the disk to particles ensures the data is irrecoverable. You may be tempted to try to, but you should know that computer experts have come a long way in retrieving data from damaged hard drives. Some organizations build redundancy into their hard drive retirement process by using multiple methods of data destruction. They may first wipe the drive using, then they could us a form of physical destruction to recover the precious metals in the hard drive for recycling purposes.